For IT admins managing hundreds—if not thousands—of employees in the cloud, implementing the right security policies can be stressful. The threat of data breaches grows each year, and the costs associated with a security breach have never been higher. Pair that with the fact that over 50% of security incidents are caused by employees’ misuse of resources, and you might just want to lock up your systems and throw away the (two-factor-authenticated, encrypted) key.
In reality, however, security in the cloud is a careful balancing act. As an admin, you have to weigh the company’s security needs against tools’ ease of use. While it’s tempting to require two-factor verification, strong password requirements, and a short idle session timeout across all your users for maximum security, you have to consider how these settings might impact employees. For those who aren’t accessing confidential data, navigating multiple security settings unnecessarily could slow them down and impact their productivity—not to mention their frustration levels. Ease access restrictions for everyone, however, and your organization’s confidential data might be at risk.
The solution? Setting up multiple authentication policies lets you custom-build the security settings you need for individual teams or groups of users, ensuring that your security settings are just right depending on each user’s role and the data they handle.
Building Out Multiple Authentication Policies For Your Organization
When it comes to managing security within your organization, there are several layers to think about. Within Trello Enterprise, for instance, there are many visibility settings admins can toggle to make sure that certain boards are only visible to certain teams or individuals. This helps ensure contractors, for instance, aren’t able to access proprietary data and no one outside Human Resources (HR) can view confidential employee information.
But what happens when the threat of data breaches isn’t internal but external?
Say a member of your finance team reused the same password across several of their personal and professional accounts—and then had those credentials stolen. (Considering 53% of people say they recycle their passwords across multiple accounts, this is a more common occurrence than you might imagine.) Whoever had their username and password combination could then access your employee’s Trello boards—and all their confidential data.
This type of security risk is exactly why many enterprises like to set stricter authentication policies for their employees. These settings can include:
- Security Assertion Markup Language (SAML) single sign-on (SSO): Synced to your external identity provider, SSO allows your users to log into multiple products—such as Jira Software, Confluence, and Trello—using just one secure log-in. This saves your employees from having to log into multiple applications while improving your enterprise’s security overall.
- Two-step verification (2SV) or multi-factor authentication (MFA): When employees sign in using two-step verification, they need to authenticate their identity using two authentication methods. Even if they successfully enter their username and password, for instance, they’ll still need to prove who they are via a second authentication step—such as entering a one-time password or code sent to their phone or email.
- Password requirements: Your password policy dictates just how complex users’ passwords need to be. If users are required to have strong passwords, they may need to include symbols, capital letters, or a certain character length in their passwords. Your password policy also dictates how often users’ passwords will expire and need to be reset.
- Idle session duration: Your organization’s idle session duration will control how long a user can stay signed into a product without conducting any activity before being automatically signed out.
Setting Authentication Policies On A Custom Basis
While security is important, not every team needs to be locked down with the strictest authentication settings possible.
That’s where the ability to create multiple authentication policies comes in handy for an enterprise. Rather than having all employees adhere to the same security standards, multiple authentication policies allow you to configure different policies for diverse user groups. That way, you can group certain users together and set the perfect security policies for their needs.
Your marketing team, for instance, may not be accessing any proprietary data or handling confidential customer information. They are, however, frequently accessing multiple tools daily and need to be able to jump in and out of projects. In their case, setting up SAML single sign-on and a strong password requirement would probably do the trick: SSO would allow them to sign in across multiple tools easily without remembering (or reusing) multiple passwords, and a strong password would help deter any breaches.
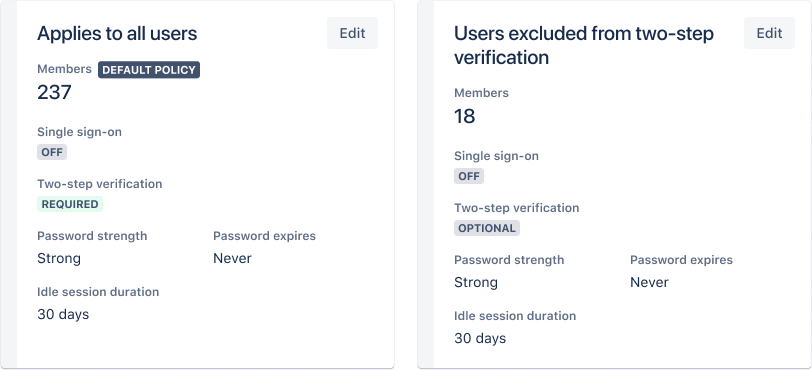
Your organization’s HR team, on the other hand, would likely require a higher level of security. Considering they handle sensitive data, it would likely make sense to turn on two-step verification for their accounts. By making them verify their identity twice while logging on, you reduce the risk of having nefarious actors (with stolen credentials) accessing your data. If the team’s employees work remotely, a shorter idle session duration also makes sense—ensuring if a user leaves their laptop open in a café or co-working space, no wandering eyes would be able to see your company’s data.
Custom-Build Your Trello Authentication Policies With Atlassian Access
As part of the Atlassian family, Trello Enterprise users can access all Atlassian Access security features, which work to bring enterprise-grade security to the Atlassian product suite, which includes Trello, Jira Software, Confluence, Bitbucket, and more.
Ready to put flexible access control in your admins’ hands? Start by heading to your Atlassian admin hub, then navigate to Security. From there, click Authentication policies, where you’ll see all your existing policies and their settings. Add new policies as needed, or edit your existing policies at the click of a button. Members can easily be added or removed from groups, and you can edit different groups’ security settings as needed to match each team’s unique needs.
How Fugro Keeps Their Trello Workspaces Secure:
As a global team of over 10,000 employees spread across 65 countries, the team of leading geo-data specialists at Fugro needs to keep their data accessible, collaborative, and secure. The team has been using Atlassian Cloud products since 2011, and Fugro’s Innovation Team uses Trello’s Kanban boards to bring innovation to life across the company.
As a worldwide company working with a plethora of clients, Fugro also needs to keep its data secure. Atlassian Access allows Fugro’s admins to standardize security policies across the company’s diverse teams, ensuring employees can do their jobs easily and efficiently while keeping data secure.
Haven’t gotten started with Atlassian Access yet? Sign up for a free 30-day trial, which will give you access to Atlassian Access’ multiple authentication policies and much more—including organization audit logs, security integrations, and active directory sync.
